
DoS (Denial of Service) attacks bombard a computer system with numerous requests exceeding the target’s capability. The attacked computer may miss important data/service requests (e.g. email messages) from outside, and suffer from limited Internet bandwidth and system resources. Denial of service is typically accomplished by flooding the targeted machine or resource, in this case the WRX560 router and the Synology NAS device with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. In this step by step guide I will show you how to enable DoS protection on your Synology WRX560 router.
STEP 1
Please Support My work by Making a Donation.
STEP 2
Login into your SRM operating system (WRX560). Go to Network Center / Security / General tab / scroll down the page until you find “DoS Protection”. Check Enable DoS protection. Check TCP, SYN and ICMP flood attack protection then click Apply. Follow the instructions in the image below.
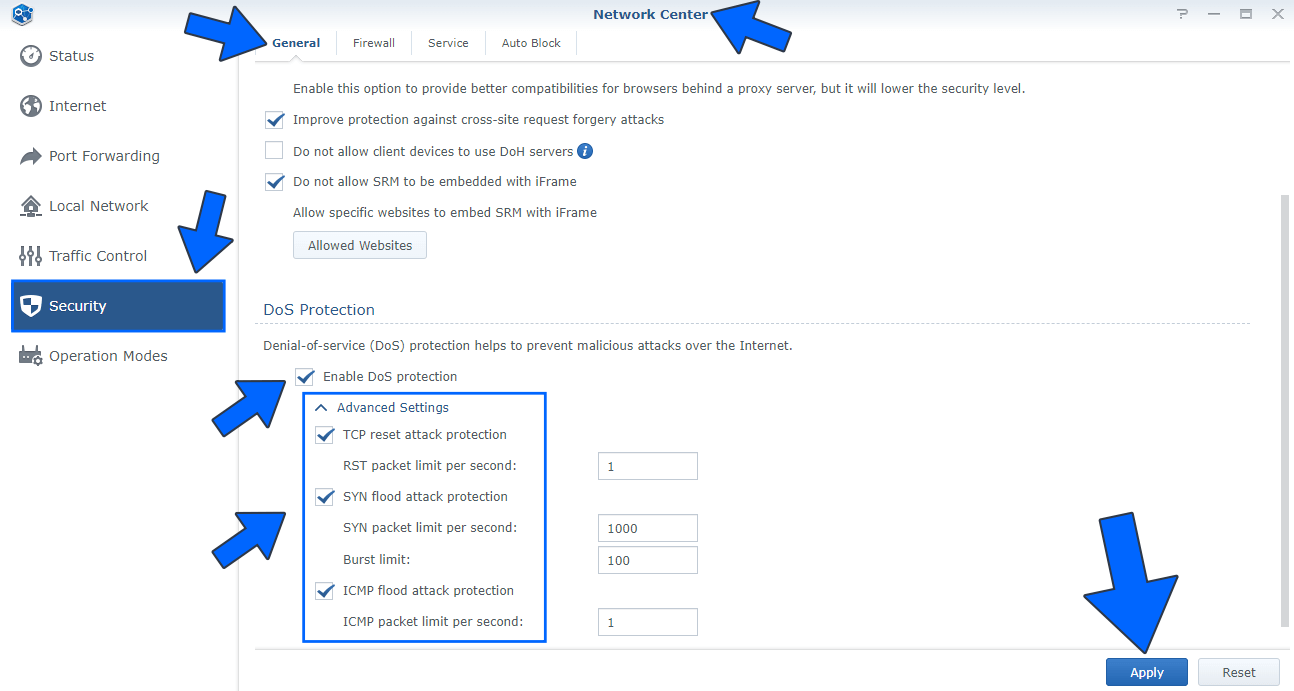
- TCP reset attack: Also known as “forged TCP reset”, “spoofed TCP reset packet” or “TCP reset attack”, is a way to tamper and terminate the Internet connection by sending a forged TCP reset packet.
- SYN flood attack: A SYN flood is a form of denial-of-service attack in which an attacker rapidly initiates a connection to a server without finalizing the connection. The server has to spend resources waiting for half-opened connections, which can consume enough resources to make the system unresponsive to legitimate traffic.
- ICMP flood attack: An Internet Control Message Protocol (ICMP) flood attack, also known as a Ping flood attack, is a common Denial-of-Service (DoS) attack in which an attacker attempts to overwhelm a targeted device with ICMP echo-requests (pings).
DoS: Short for Denial of Service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. Many DoS attacks, such as the Ping of Death and Teardrop attacks, exploit limitations in the TCP/IP protocols. For all known DoS attacks, there are software fixes that system administrators can install to limit the damage caused by the attacks. But, like viruses, new DoS attacks are constantly being dreamed up by hackers.
DDoS: In a DDoS attack the incoming traffic flooding the victim originates from many different sources – potentially hundreds of thousands or more. This effectively makes it impossible to stop the attack simply by blocking a single IP address; plus, it is very difficult to distinguish legitimate user traffic from attack traffic when spread across so many points of origin.
Summing up: A Denial of Service (DoS) attack is different from a DDoS attack. The DoS attack typically uses one computer and one Internet connection to flood a targeted system or resource. The DDoS attack uses multiple computers and Internet connections to flood the targeted resource. DDoS attacks are often global attacks, distributed via botnets.
Note: How to Enable DoS Protection on the RT2600ac and MR2200ac routers.
Note: How to Enable DoS Protection on RT6600ax router.
This post was updated on Monday / August 11th, 2025 at 2:41 AM
