
Below I will explain how I reduced the number of direct attacks on my Synology NAS by correctly setting up the GeoIP Firewall on the powerful DSM operating system. I blocked all geographical regions except for my own, my static IP and my subnet mask. Most brute force attempts come from outside my home country, Romania. With these detailed settings below you will not only reduce the number of attacks received on port 22, like SSH login attempts, and the associated notifications received for said attacks, but also bring them down to almost 0. I thought I’d share how to implement the Firewall GeoIP protection for others wanting to reduce the surface area for attacks and make their Synology NAS device that much more secure.
You will have to follow the scheme below exactly as it is: allow, allow, allow, deny. And the order of insertion must be followed faithfully! I’ve been running these firewall settings on my Synology NAS with geo IP deny rules for about a month now and everything seems to be working fine as I’ve had no unauthorized login attempts in my Log Center from any of the countries I’ve denied.
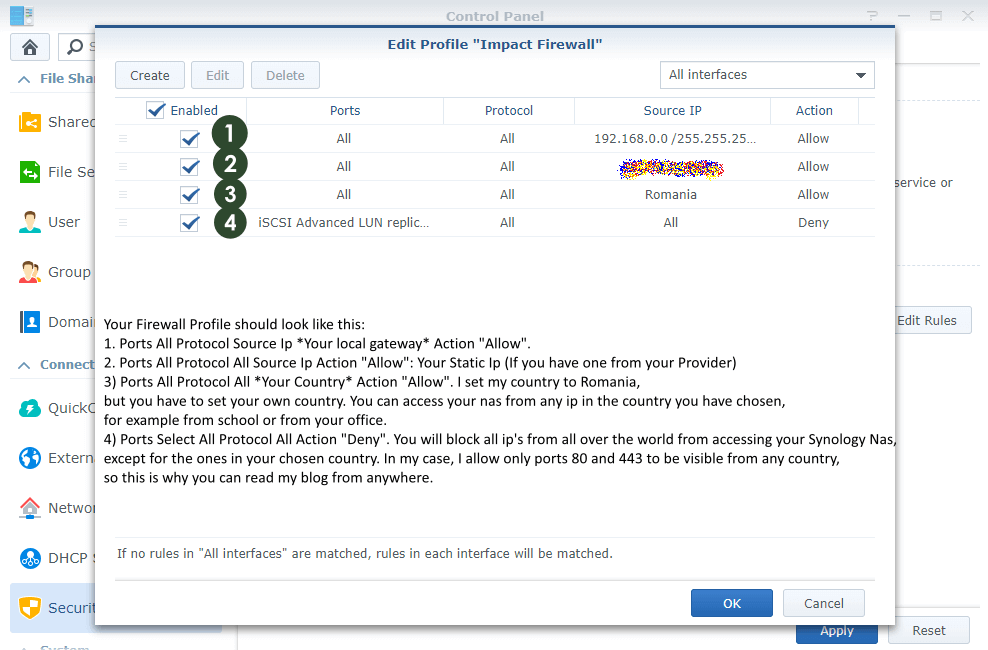
After you finish completing all the STEPS in this article, your Firewall profile should look like this:
- Ports All – Protocol All – Source IP: “Your Subnet Mask” 192.168.0.0/255.255.255.0 Action: Allow.
- Ports All – Protocol All – Source IP: “Your Static IP” Action: Allow (Set your Static IP if you have one from your Provider.) I strictly recommend having a static IP if you are using a Synology NAS.
- Ports All – Protocol All – Source IP: “Your Country” Action: Allow I set my country to Romania, but you have to set your own country. You can access your NAS from any IP in the country you have chosen to allow, for example from an IP from school or from your office.
- Port All – Protocol All – Source IP All – Action: Deny. You will block all IPs from all over the world from accessing your Synology NAS, except for the ones in your chosen country. In my case, I only allow ports 80 and 443 to be visible from any country, so this is why you can read my website from anywhere.
- Warning: The order of insertion must be respected faithfully. Rules are prioritized according to their positions in the list.
STEP 1
Please Support My work by Making a Donation.
STEP 2
Go to Control Panel / Security / Firewall and follow the instructions in the image below.
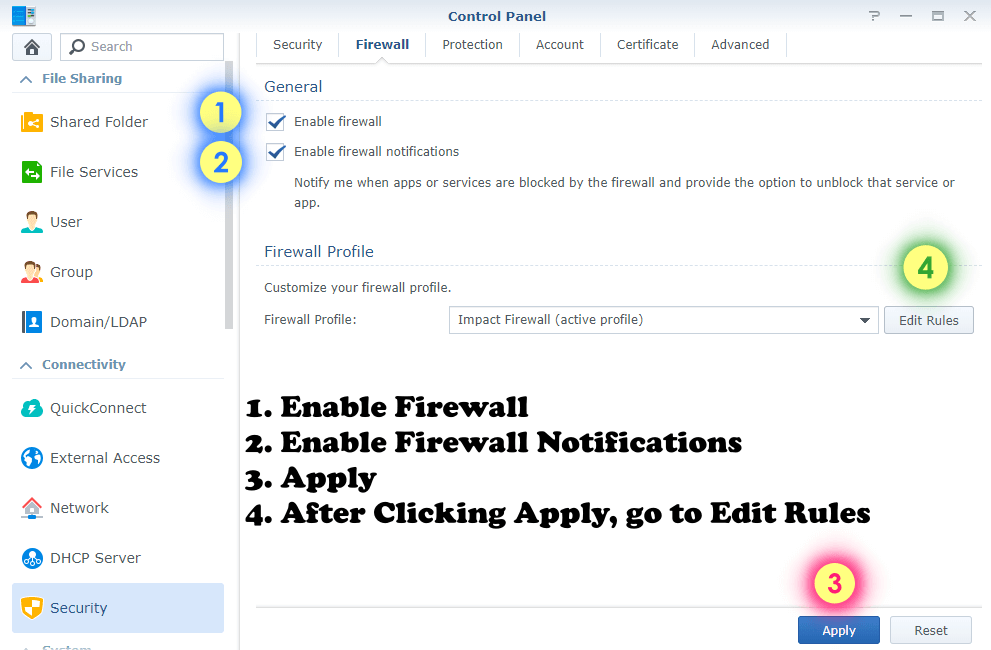
STEP 3
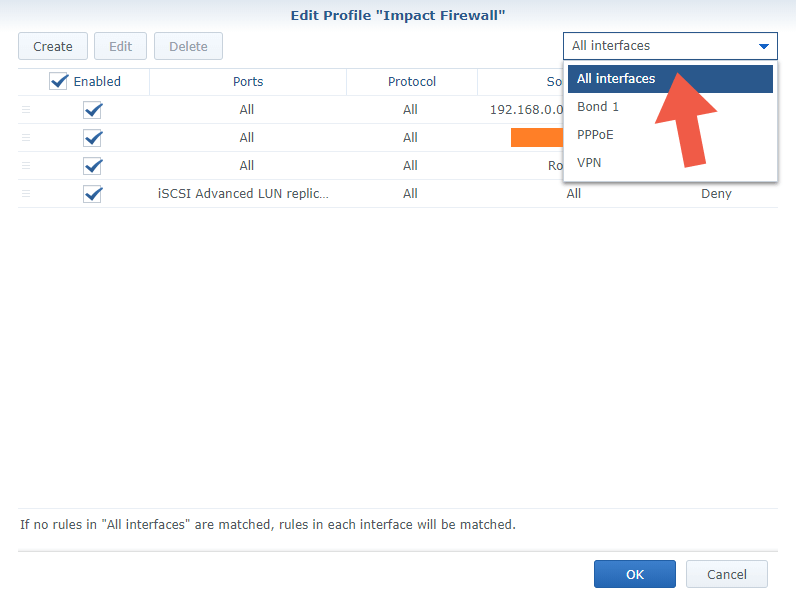
After Clicking Apply go to “Edit Rules” / Create. Follow the instructions in the images below. In the drop-menu at the top right of the page Select “All interfaces”. Please disregard existing rules in the screenshot below – these will be created in the following steps using your preferences.
STEP 4 (Rule 1)
Follow the instructions in the images below to add the first Firewall rule. Create your first firewall rule to allow your internal/home network.
Image 1
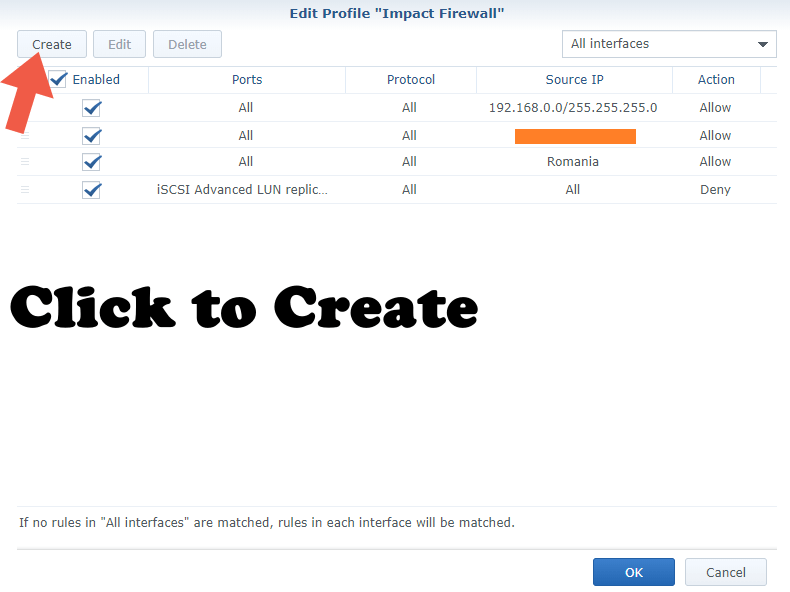
Image 2 (Read Note E at the end of the article)
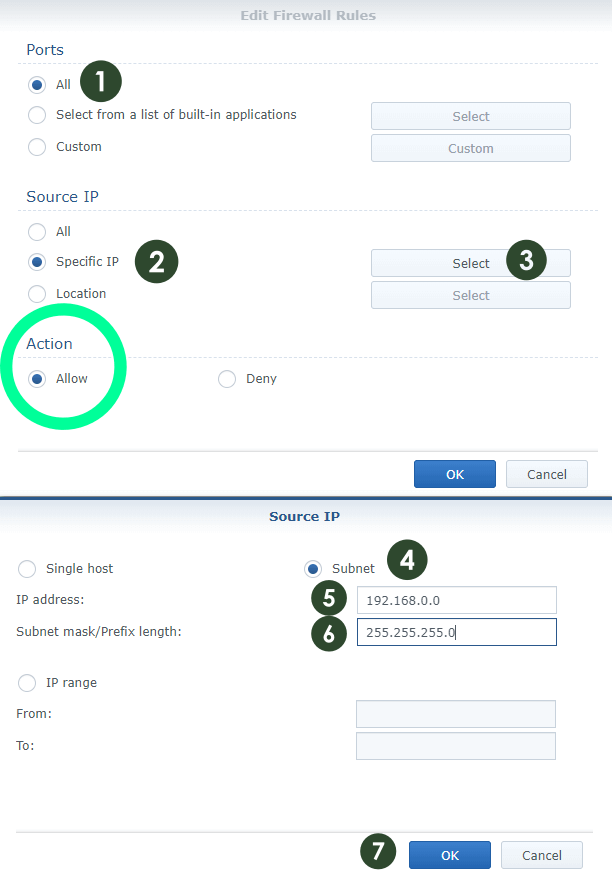
STEP 5 (Rule 2)
Follow the instructions in the images below to add the second Firewall rule. Create your second firewall rule to allow your Static IP “WAN” from your ISP (Internet Service Provider), if you have one.
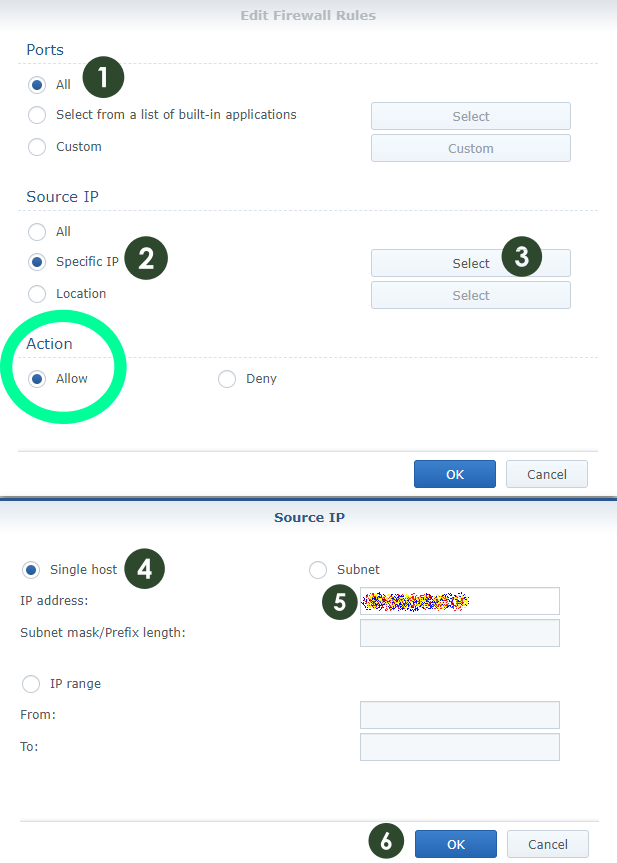
STEP 6 (Rule 3)
Follow the instructions in the images below to add the third Firewall rule. Create your third firewall rule to allow your own Country.
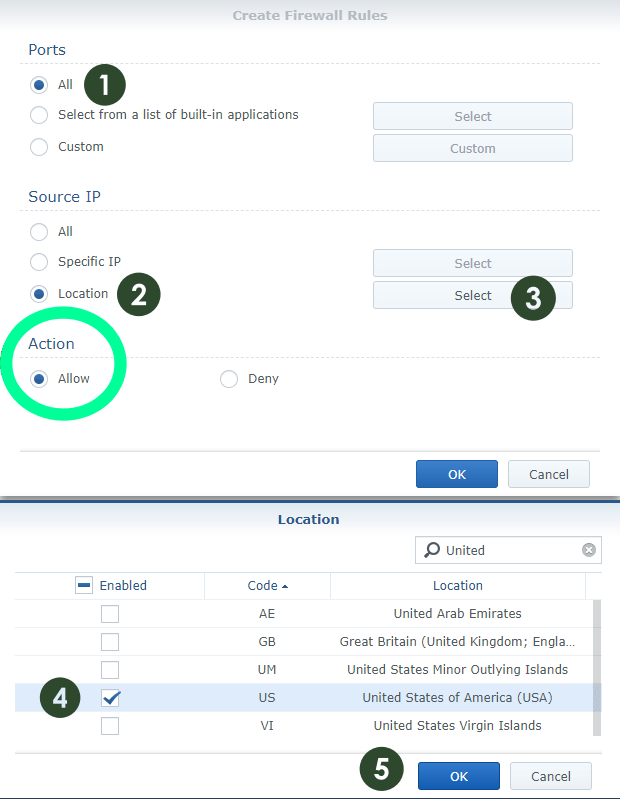
STEP 7 (Rule 4)
Follow the instructions in the image below to add the fourth Firewall rule. Create your fourth firewall rule to deny all other countries/locations.
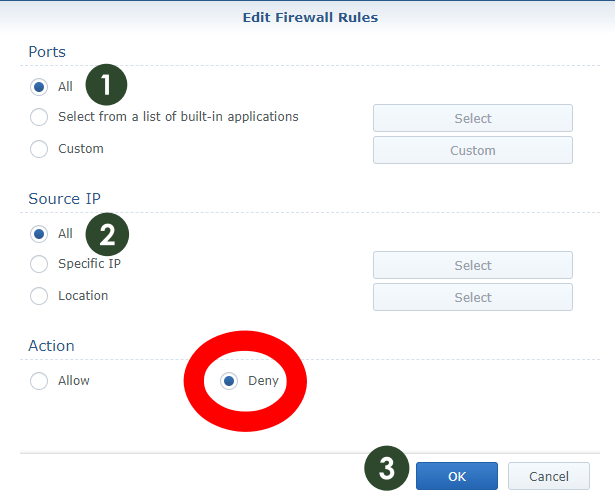
STEP 8
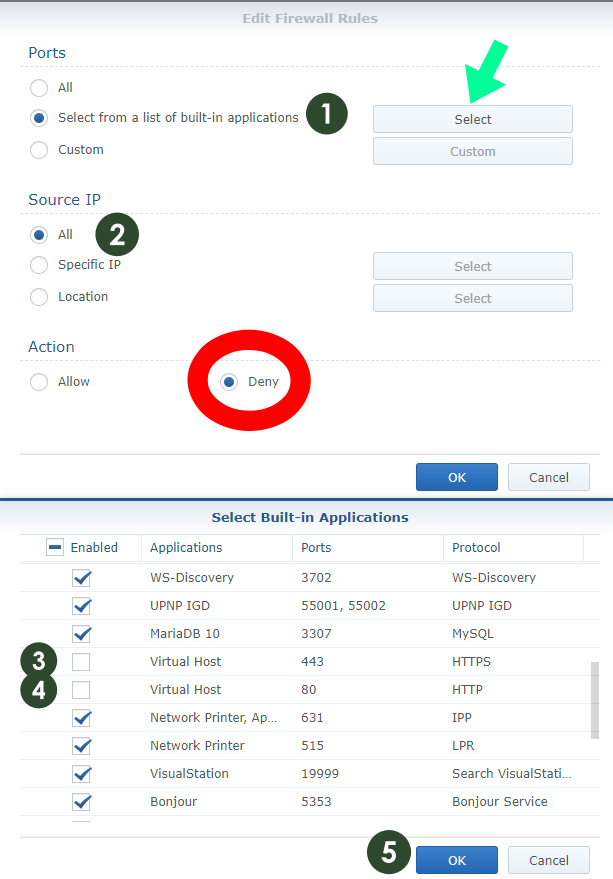
If you are using your Synology NAS for web hosting, or if you have a service which must be accessible to all, follow the instructions in the images below. As mentioned above, if you are using your Synology NAS for web hosting, MailPlus server etc., you have to go through a list of built-in applications and exclude your service. In my case, I excluded port 80 and port 443 from the Deny list to make my website accessible from all over the world. In the “Select from a list of built-in applications” you can choose which app/port/services can be accessible from all countries/locations.
Test-reach your Synology NAS on your internal network and from external networks in your country like your office, school or a free Wi-Fi area. You can also make sure (validate) if the firewall is working and blocking denied countries/locations by using a Tor browser or a VPN service to send traffic from a different country. Alternatively you can contact a friend from another part of the world by providing him with your Synology QuickConnect or DDNS address. If they can’t connect, that means the firewall setup is working perfectly. These tests will help you see if your firewall rules are working properly. Contact me by leaving a message if you have any problems regarding the Firewall Rules.
Note A: Firewall rules are executed top to bottom. Meaning that all “Allow” rules must be at the top of the list, with a “Deny” rule at the bottom. When traffic enters the NAS, it will go through the list and, if it isn’t explicitly permitted, the “Deny” rule will block the traffic.
Note B: If you don’t have a static IP and you have a dynamic IP that changes every time you connect, set up only Rule 1, Rule 3 and Rule 4 described in this article.
Note C: If you set up only Rule 1 and Rule 3 because you have a dynamic IP, you can connect to your NAS via VPN if you are planning to visit other countries, or you can allow your destination country on Rule 3 before leaving your own country.
Note D: If you don’t allow your own Country on Rule 3, you will receive this message: Your computer has been blocked by the new firewall configuration. The firewall configuration has been reset to the previous state. Please make sure that no rule is blocking your computer and try again.
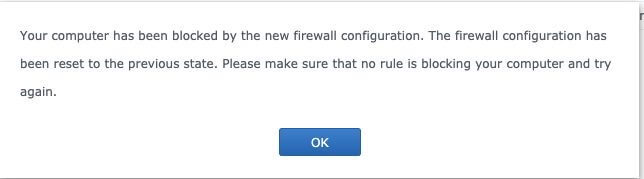
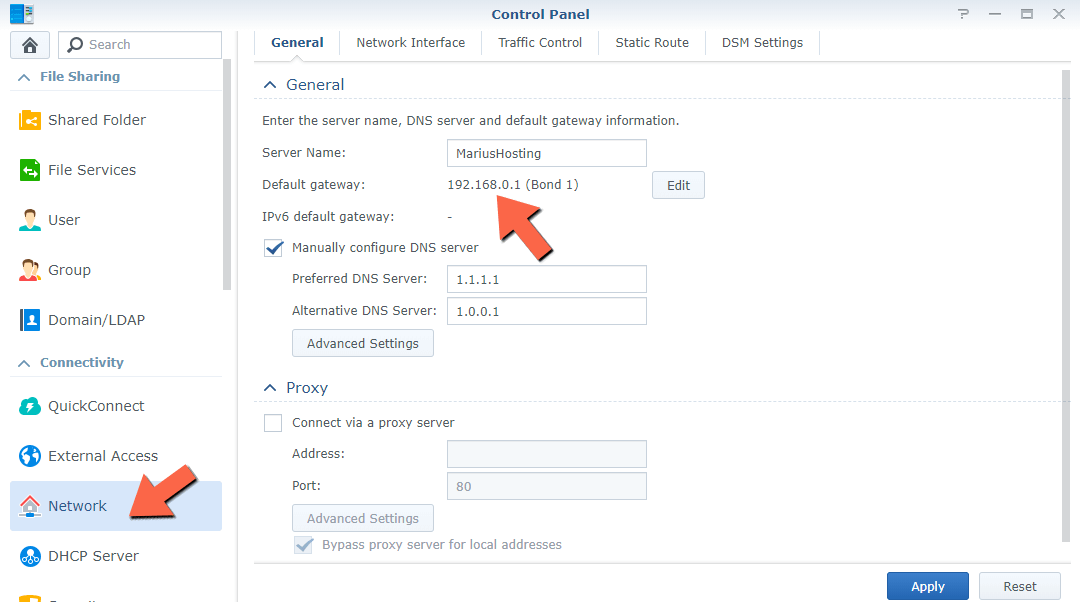
Note E: If you continue to see the message “Your computer has been blocked by the new firewall configuration” when you save your rules, it means that Rule 1 on STEP 4 is not set up correctly. In my case, my Default Gateway is 192.168.0.0 but you might have a different Default Gateway. Discover what is your Default Gateway in Control Panel / Network / General / Default Gateway. So on STEP 4 Rule 1 (Image 2) you have to set YourDEFAULTgatewaynumber/255.255.255.0
Note F: As you add new packages to your NAS, new “Allow” rules will need to be created. Your NAS will generally inform you that you need to create a new rule when you finish installing/configuring a new package.
This post was updated on Sunday / December 3rd, 2023 at 4:03 AM
