The concept of file transferring in computer networks is probably as old as email itself, if not older. There are many ways and protocols used for file transferring in Synology NAS and technologies have evolved over the last few years. One file transfer protocol, which became a standard since 16 April 1971, is FTP (File Transfer Protocol). FTP is a protocol for transferring files via a network (typically a TCP/IP one, like the Internet). Activating FTP in your Synology NAS becomes mandatory if you are thinking about hosting your blog directly from home without paying a hosting provider anymore, like I do. When you host your website from home you have total control, you are the real Sysadmin. Below we will discover the differences between FTP, SFTP and FTPS.
What is FTP and how does it work?
FTP is a traditional client-server application. Users connect to an FTP server (using its IP, local Lan IP or domain name) via a client like FileZilla. FTP uses two connections. One for sending and receiving commands (port 21) and another for data transferring (port 20). Connected clients can issue standard directory navigation commands, such as list or cd or get and put, to download or upload a file in the Synology Server via FTP. In the FileZilla client the process of navigating the files and directories is similar to that of a local file browser. Uploading and downloading files with get and put is a matter of a simple drag and drop. User authentication is done via username and password or via an anonymous guest account previously created in your Synology NAS. FTP sites are usually named as local LAN ip or your Domain name previously set up in your Synology NAS.
What is SFTP and why is it better?
SFTP (Secure File Transfer Protocol) is part of the SSH software suite and provides secure file transfers. It is also a client-server application like FTP, but with the following significant enhancements:
- Encrypted communication: Unlike FTP, SFTP provides secure file transfers by using a SSH’s (Secure Shell) PKI security mechanism. It uses a known-hosts file to determine the server’s authenticity. The very first time you connect to a server, the server sends its public key to the client. Users can either login without providing a password (by configuring the private/public keys) or by using a username and a password.
- Interrupted transfers can be resumed whenever you want: One of the main pains of FTP was that it did not support resumed downloads. Whenever a file transfer would get interrupted, whatever the cause, the user would have to re-initiate the downloading process, starting it all over again from the very beginning. SFTP clients can detect partial downloads and resume them if the user requests to download the same file again.
- Mass simultaneous file download: SFTP supports wildcards when referring to files being downloaded through the mget command.
- Advanced file operations: SFTP feels more like a shell than an FTP client. It allows changing permissions remotely, taking ownership of files and directories, as well as creating and deleting them.
What is FTPS?
Concern for Internet security amplified during the 1990s. In response, Netscape created the Secure Sockets Layer (SSL, now known as TLS) protocol to protect communications over a network. SSL was applied to FTP to create FTPS. Like FTP, FTPS uses two connections: a command channel and a data channel. You can choose to encrypt both connections or only the data channel.
FTPS authenticates your connection using a user ID and password, a certificate, or both. When connecting to a trading partner’s FTPS server, your FTPS client will first check if the server’s certificate is trusted. The certificate is considered trusted if it was either signed by a known certificate authority (CA) or if it was self-signed by your partner and you have a copy of their public certificate in your trusted key store. Your partner may also require that you supply a certificate when you connect to them. If your certificate isn’t signed by a third-party CA, your partner may allow you to self-sign your certificate, sending them the public portion beforehand to load into their trusted key store. User ID authentication can be used with any combination of certificate and/or password authentication. Your Synology NAS device allows you to activate any of the three options mentioned above. I strongly recommend that you only activate the SFTP if you host your WordPress blog from home. This will help you to create backups and will allow you to safely download WordPress plugins.
What’s the difference between FTPS and SFTP?
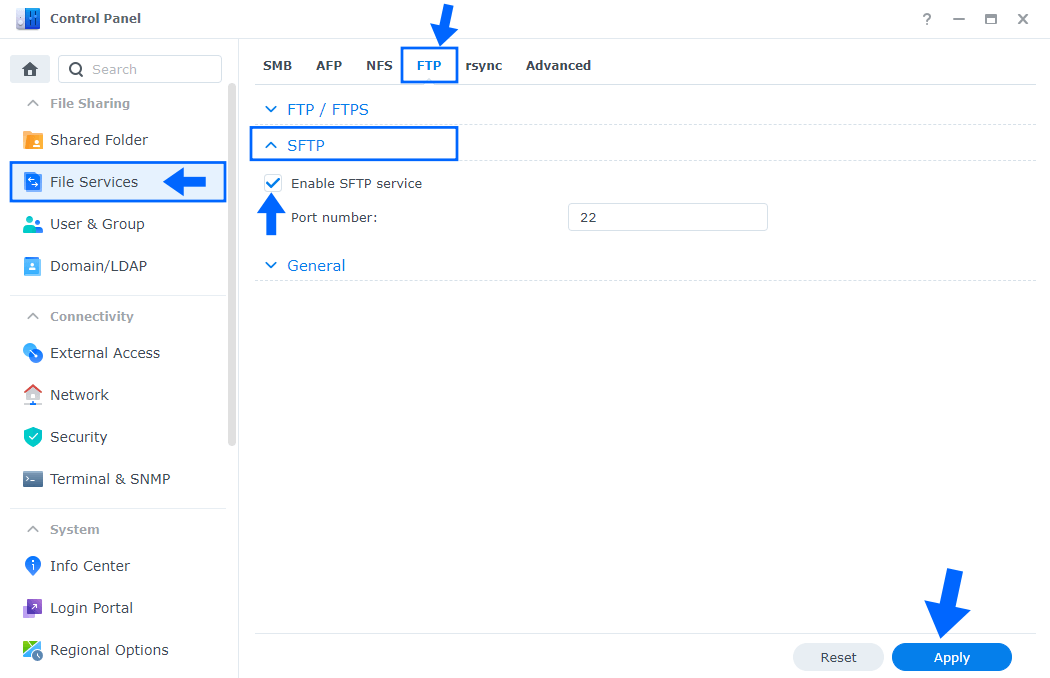
Both FTPS and SFTP offer strong protection through authentication options that FTP can’t provide. So why should you choose one over the other? One major difference between FTPS and SFTP is that FTPS uses multiple port numbers. The first port for the command channel is used for authentication and passing commands. However, every time a file transfer request or directory listing request is made, another port number needs to be opened for the data channel. In the screenshot below I have activated SFTP.
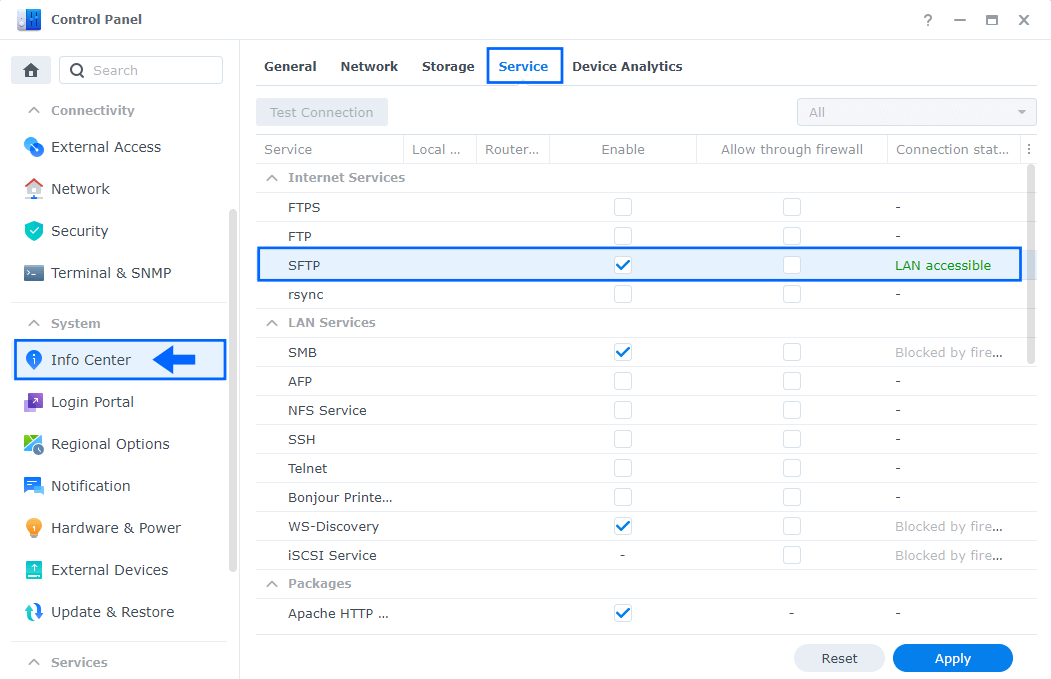
You and your trading partners will therefore have to open a range of ports in your firewalls to allow for FTPS connections, which can be a security risk for your network. SFTP needs only a single port number for all SFTP communications, making it easy to secure. While both protocols have their benefits, I recommend SFTP when you activate it on your Synology NAS thanks to its better usability with firewalls.
Always remember that, when activating the protocol of your choice, whether it’s FTP, SFTP or FTPS, port-forwarding on your router is a must. For example, if you want to activate FTP on your Synology NAS, you need to open port 21 on your router, both TCP and UDP. If you want to activate SFTP on your Synology NAS, you need to open port 22 on your router. And if you want to activate FTPS on your Synology NAS, you need to activate port 21 and another port up to 56047.
This post was updated on Saturday / February 8th, 2025 at 2:20 PM