I just want to inform you that a new variant of Specter was discovered, one that puts Windows, Linux and ChromeOS systems at risk. It is a vulnerability that affects Intel CPUs and puts the privacy and security of users at risk. This failure could allow malicious software to access privileged memory and read content within the operating systems. Andrei Vlad Lutas, a Bitdefender researcher, discovered this vulnerability and called it SWAPGS. CVE-2019-1125, also referred to as the “SWAPGS” vulnerability, was made public on 6th of August 2019 as a new variant of Spectre V1 affecting Windows and Linux systems equipped with Intel processors. Intel was informed a year ago about this vulnerability.
Now this problem has already been solved at the software level through security patches. No CPU microcode updates are required. To avoid this vulnerability we can update the system at the software level . Windows users have to update with the latest security patches that came out on July 9. At the moment I can’t find any information regarding CVE-2019-1125 in the latest DSM Synology patch 6.2.2-24922 Update 2. This issue is not believed to be exploitable in the Linux kernel, but I think kernel updates will be made available to ensure that it cannot be exploited.
I have already sent a support ticket to Synology and I look forward to an answer that I will be publishing in this article.
Fortunately, in practice, exploiting the SWAPGS vulnerability appears quite difficult, but upgrading to a patched kernel is certainly recommended.
Bogdan Botezatu, director of threat research and reporting at Bitdefender, says “an under-documented instruction that makes the switch between user-owned memory and kernel memory.” Botezatu also says that, at this point, “all Intel CPUs manufactured between 2012 and today are vulnerable to the SWAPGS attack.”
Update: 09.08.2019
After contacting Synology, here is the answer I received through their support channel, today 9 August 2019.
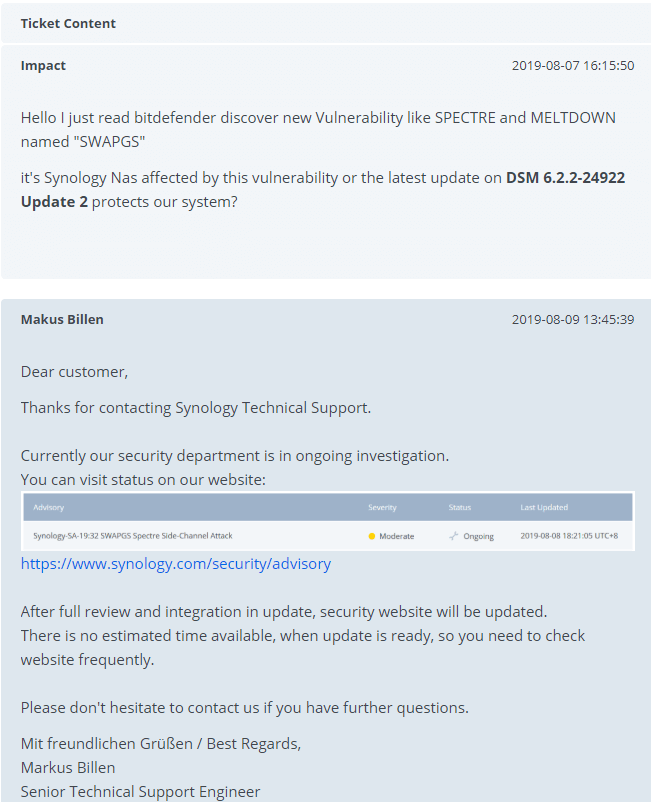
Here is the screenshot taken from Synology Security Advisory.
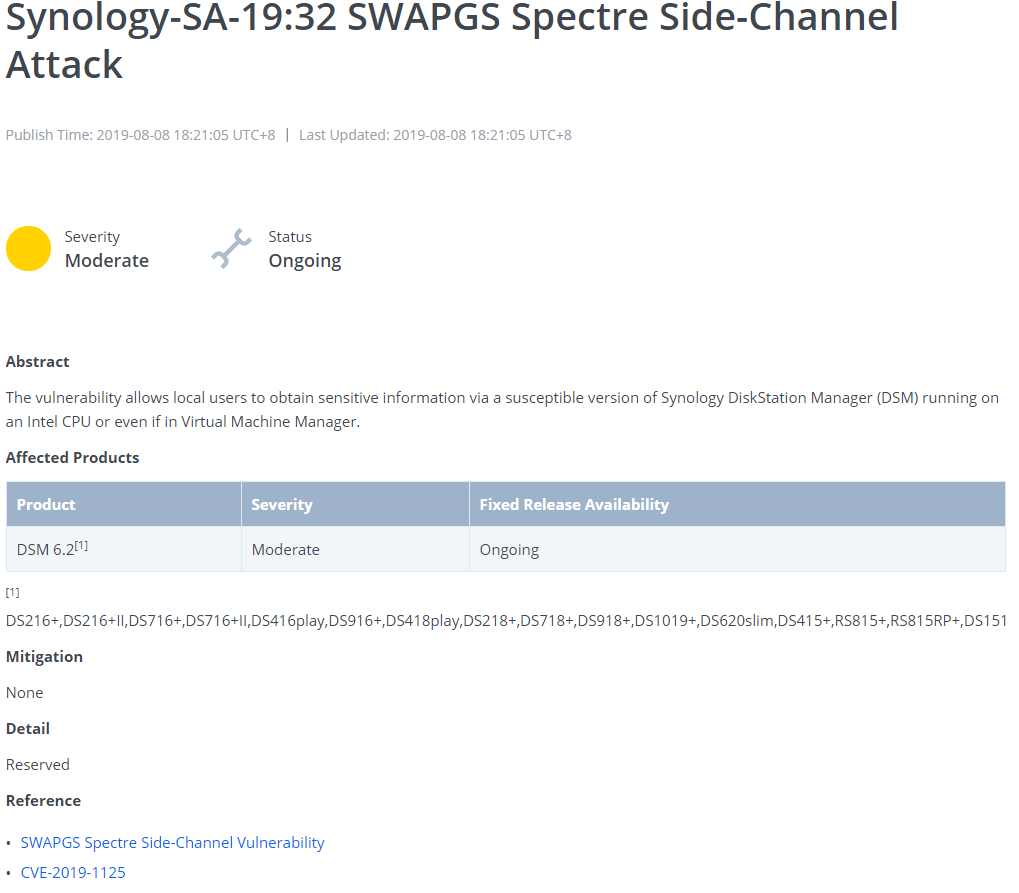
Right now this vulnerability (SWAPGS) affects Synology Products with a DSM 6.2 operating system with an Intel CPU. The vulnerability impacts the following models:
DS216+,DS216+II,DS716+,DS716+II,DS416play,DS916+,DS418play,DS218+,DS718+,DS918+,DS1019+,DS620slim,DS415+,RS815+,RS815RP+,DS1515+,DS1815+,DS1517+,DS1817+,DS2415+,RS2416+,RS2416RP+,RS818+,RS818RP+,RS1219+,DS1618+,RS2418+,RS2418RP+,RS2818RP+,DS2419+,DS1819+,DVA3219,RS3413xs+,RS10613xs+,RS3614xs+,RC18015xs+,RS18016xs+,RS3617xs,RS3614xs,RS3614RPxs,,RS3617RPxs,RS3617xs+,DS3617xs,DS3018xs,RS4017xs+,RS18017xs+,RS3618xs,FS1018,FS2017,RS1619xs+,SA3400,FS3400,FS3017
I will be back with more information as soon as the update is released.
This post was updated on Wednesday / November 6th, 2019 at 2:41 AM
