Have you recently downloaded and manually installed this update patch for your Synology router, the RT2600ac, or your Mesh router, the MR2200ac? The updated patch called sha256sum, code name Synology-SA-19:16 Dragonblood, helps prevent a Dragonblood attack.
What are Dragonblood Attacks? Dragonblood attacks CVE-2919-9494 and CVE-2019-9496 allow remote attackers to obtain sensitive information or conduct denial-of-service attacks via a susceptible version of Synology Router Manager (SRM), the operating system for Synology routers and Mesh routers.
CVE-2019-9495, CVE-2019-9497, CVE-2019-9498 and CVE-2019-9499 allow remote attackers to obtain sensitive information via a susceptible version of the RADIUS Server.
If you run Security Advisor on the RT2600ac router or the MR2200ac Mesh router after installing the patch, you will receive a Critical Alert like this one:
“The following file(s) have been modified: /usr/bin/hostapd, /usr/bin/hostapd_cli, /usr/sbin/wpa_cli, /usr/sbin/wpa_passphrase, /usr/sbin/wpa_supplicant. Please check whether uncertified third-party packages have been installed.”
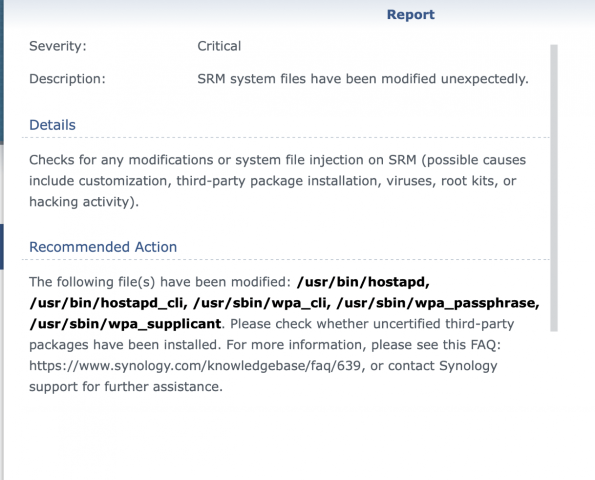
The official response from Synology Support is:
“The warning message that you provided is known by our developers and is caused by installing the security patch for the issue “Dragonblood”, to do with WPA3 security on Wireless networks. This message is expected to be shown and can be ignored.”
Just thought you’d all like to know. This is a known issue and Synology developers are already working on it to prevent future false alarms like this one.
This post was updated on Thursday / September 2nd, 2021 at 12:22 AM
